Threat Hunting – What is it and is it worth doing?
- By Paweł
In recent months, we have been observing a growing number of inquiries from our clients and business partners regarding Threat Hunting. The questions are very specific: what exactly is Threat Hunting, what effects does it bring, how is it conducted, and – most importantly – is it worth implementing in your organization?
We are therefore sharing the answer in the form of this article – from our perspective as a company that provides professional cybersecurity services, including advanced Threat Hunting activities.
What is Threat Hunting?
Threat Hunting is the proactive search for signs of an adversary’s presence in the IT environment – before, if at all, defense systems (such as antivirus or EDR) raise the alarm. It is the process of analyzing data from the IT infrastructure to detect hidden, hard-to-see incidents that may indicate the presence of an attacker, APT-type activities, or unauthorized internal activities.
Threat hunting is fundamentally human-centric. While tools and automation play a supporting role, the core of threat hunting relies on the expertise, intuition, and analytical skills of cybersecurity professionals. Threat hunters proactively search for threats that have bypassed automated security systems, requiring them to understand attack techniques, analyze data, and develop hypotheses about potential malicious activity.

Unlike reactively responding to alerts, Threat Hunting is an active investigative process that aims to reveal threats that have gone unnoticed by standard security mechanisms.
Threat Hunting allows you to:
- detect threats that have bypassed automatic protections (e.g. fileless attacks, C2 activity, lateral movement),
- identify attacker activity at an early stage (before data leaks occur, for example),
- confirm or rule out hypotheses regarding suspicious activities in the network,
- improve the operation of SIEM/EDR systems by calibrating and creating new detection rules.
In short: Threat Hunting increases the organization’s ability to defend against advanced threats – and this before they cause damage.
When describing our topic, we cannot fail to mention Breach Detection Gap. What is Breach Detection Gap? It is the time that elapses from the moment an attacker breaches a system until it is detected by the organization. According to various reports (e.g. Mandiant or IBM), this time can be as long as several dozen days – which gives the attacker comfort for further penetration, data exfiltration or lateral movement.
Breach Detection Gap
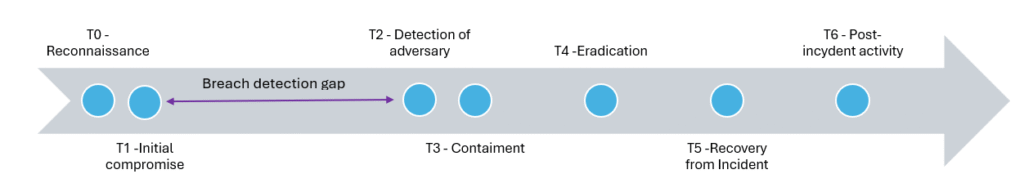
Threat Hunting helps reduce the Breach Detection Gap (the time between an intrusion and its detection) by proactively looking for signs of attackers’ presence in the IT environment. Threat hunters analyze telemetry data such as logs, looking for anomalies and techniques known from MITRE ATT&CK. This allows them to detect hidden or advanced threats that have bypassed automated mechanisms. By reducing the time to detect an incident, an organization can respond faster and limit the potential damage. Threat Hunting fills the gap where prevention and automatic detection fail.
Types of Threat Hunting
Data-driven hunting
A hunt initiated based on the analysis of existing data (e.g. proxy logs, netflow). The hunter formulates hypotheses based on anomalies or unusual patterns — e.g. unknown User-Agents in logs or unexpectedly large data transfers.
Intelligence-driven hunting
An approach based on Threat Intelligence (feeds, IoC). The hunter operates based on specific intelligence data: IP addresses, hashes, domains that appeared in threat reports, and searches the environment for them.
Entity-driven hunting
Focus on specific entities — hosts, accounts, systems. The goal is to thoroughly analyze the behavior of these objects. The hunter focuses on the “object”, observing any unusual activities around it.
TTP-driven hunting
Based on Tactics, Techniques, Procedures (e.g. from MITRE ATT&CK). Looks for signs of specific attack techniques used — e.g. lateral movement, PowerShell, SMB exploitation. This is a targeted hunt for specific adversary patterns.
Hybrid hunting
And finally, our favorite type. Combines approaches: data + intelligence + TTP + entity analysis. Integrates different approaches into one process to achieve a more comprehensive and effective result.
Threat hunting is fundamentally human-centric.
We know that Threat hunting is fundamentally human-centric. So what does our Threat Hunter need to know and most importantly, how should it find threats?

Threat Hunter requirements
- Experience in log analysis and incident detection and response in network and application environments
- Knowledge of techniques and tools used for threat hunting and incident monitoring and response
- Knowledge of TTP (Tactics, Techniques, Procedures) used by cybercriminals and the ability to use this knowledge in the threat hunting process
- Ability to cooperate with the Threat Intelligence team and use their knowledge to detect advanced threats
- Knowledge and experience in working with operating systems, networks and protocols, as well as basic IT services (e.g. DNS, DHCP, SMTP, etc.)
How to effectively detect anomalies in data?
We already know what skills a good Threat Hunter should have, at least the basic ones. It’s time to look at how he will search for threats. There are 4 most common methods for searching for anomalies:
Statistical analysis
Involves detecting deviations from the norm based on statistics such as the mean or standard deviation.
Example: if there are usually 10 logins per hour, and suddenly 100 appear, this is a potential anomaly.
Clustering
Identify unknown patterns or anomalies by grouping similar behaviors or events.
Example: similar network traffic flows or user activities
Grouping (Aggregation)
Summarize large data sets to identify trends or spikes
Example: Grouping logs by source IP or grouping alerts by type.
Searching (Filtering and Querying)
Look for known Indicators of Compromise (IoCs), suspicious strings, or matching attack signatures.
Example: Searching logs for specific hashes, IPs, or suspicious commands.
What is the result of Threat Hunting?
We already know what Threat Hunting is, we know who and how should do it. So we have to answer what is it all for? What will we gain by doing threat hunting?
Each hunt ends with specific conclusions. Depending on the facts detected, these may be:
- analysis reports and recommendations for changes,
- detection of an active security incident and its escalation to the IR team,
- new detection rules for the SIEM/EDR system (e.g. KQL queries, ruleset),
- proposals for changes to system configuration (hardening),
- confirmation of the lack of signs of an attack – which is also valuable information.
As seen above, threat hunting is a valuable source of knowledge about threats and an excellent complement to automatic detection methods. Using analysis techniques such as clustering, grouping, searching, and statistical analysis, analysts can detect hidden threats that escape rules-based systems alone. This is a proactive approach that allows for a better understanding of the environment and faster response to incidents.
Is this for me and my organization?
Threat Hunting is not reserved for corporations only. It can be particularly useful for:
- companies from the medical, legal and financial sectors – due to sensitive data,
- software houses and technology companies – due to the risk of espionage or code theft,
- MSPs (small and medium-sized enterprises) that have implemented EDR systems but want to make the most of their capabilities,
- organisations with compliance requirements (e.g. ISO 27001, NIS2, GDPR),
- companies after a security incident – as an element of sanitisation and prevention of further threats.

Threat Hunting is not just a buzzword – it is real support for the security of an organization. It helps to see what is hidden and act before it is too late.
If you want to find out what Threat Hunting could look like in your company – please contact us. We will conduct an initial assessment and show you what such a process could look like in your IT environment.
